Photo by Shubham Dhage on Unsplash
Computer Networking: A Beginner's Guide for a Deep Dive
Learn about the Internet, Protocols, IP Addresses and the TCP/IP and OSI Model
In this article, we will cover how the internet started, what is the internet, and the rules that govern the internet. Different protocols, when they are used and what are their significance. We will go into the TCP/IP Protocol and the OSI Model. We will learn how data is transferred and received over the net and the devices involved. Gain insights on IP Addresses and Port Numbers.
What is the Internet?
In simple terms, it is the Interconnection of devices over the Network. Let's understand these two terms:
Interconnection: It means the connection or a link set up between two devices so that they can communicate with each other. It can be a simple wire.
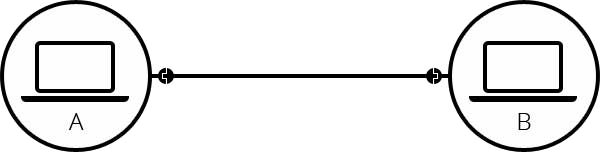
Network: It refers to a collection of interconnected devices, such as computers, servers, routers, switches, and other networking equipment, that are linked together to enable communication and data exchange.
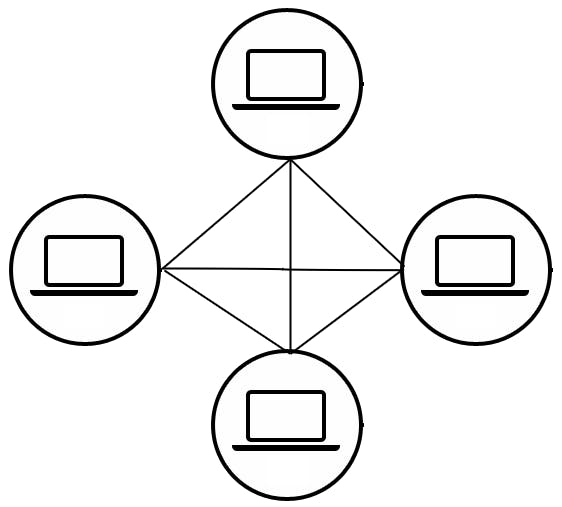
It means the Internet is such a collection of devices within a network that can communicate with each other.
Communication can be done in two ways:
Guided Ways: Here the path is defined. Like wires, optical cables, etc.
Unguided Ways: Here the path is not defined, it majorly uses wireless connections. Like Wifi, Bluetooth, etc.
Evolution of the Internet:
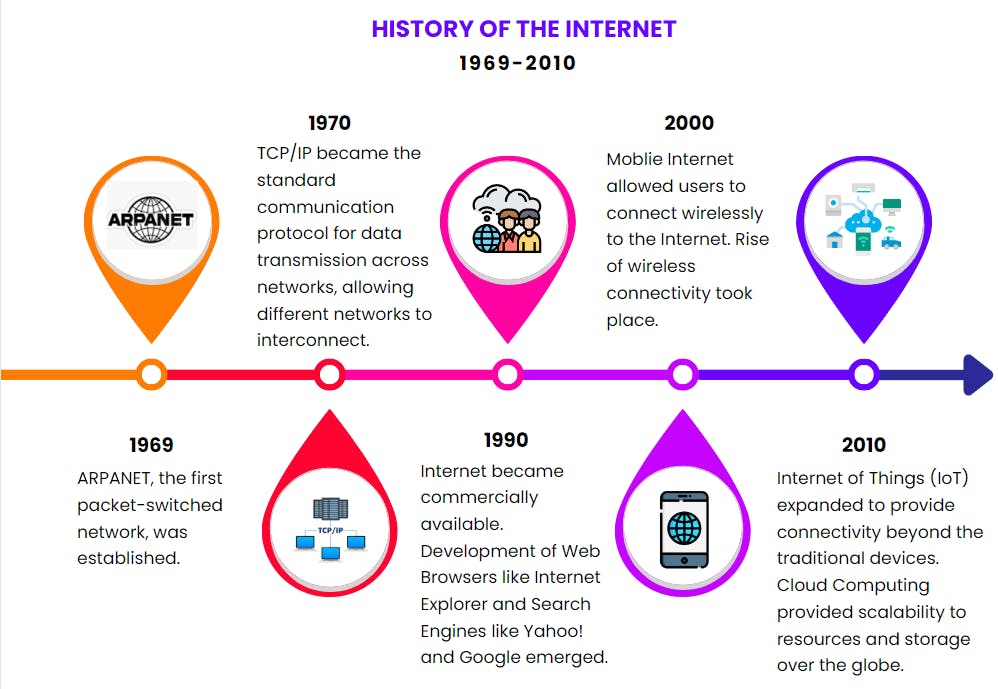
Link to the world's first website.
Now we know about how computers are connected in a network. Let's understand the different ways how these computers are connected. This arrangement of computers is called network topology.
Network Topology
Network topology refers to the physical or logical arrangement of devices, connections, and nodes in a computer network. It indicates the type of connection and how communication happens between devices.
Bus Topology
All devices are connected to a single communication line, known as a bus.
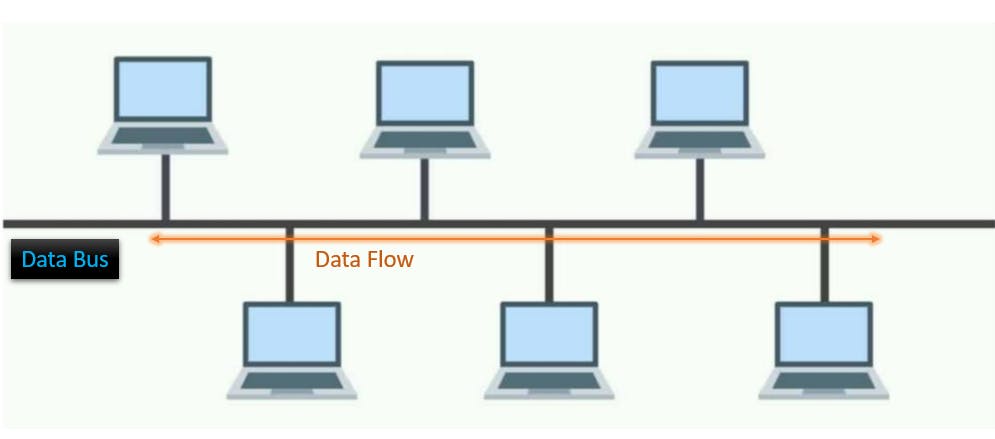
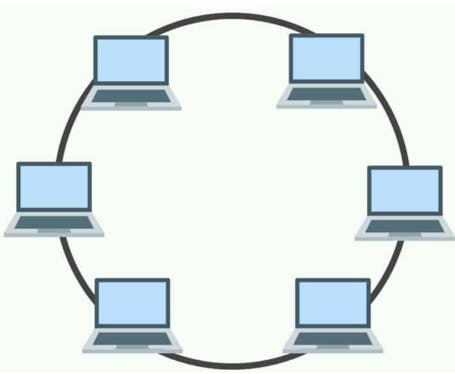
Ring Topology
Here devices are connected in a closed loop or ring formation. Each device is connected to its neighbouring devices, and data circulates the ring in one direction.
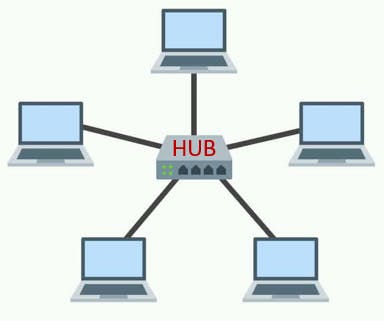
Star Topology
All devices are connected to a central hub or switch. Each device has a dedicated connection to the central hub. The Central hub acts as a communication mediator, relaying messages between devices.
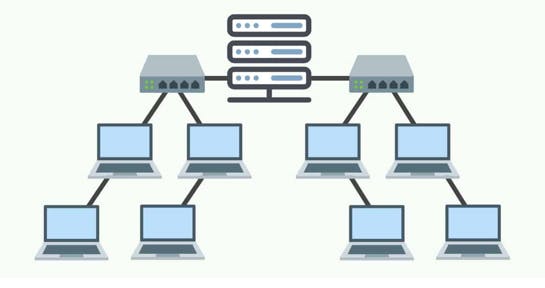
Tree Topology
It is a hierarchical arrangement of devices, in a tree-like structure. It consists of multiple levels, where devices at lower levels are connected to devices at higher levels.
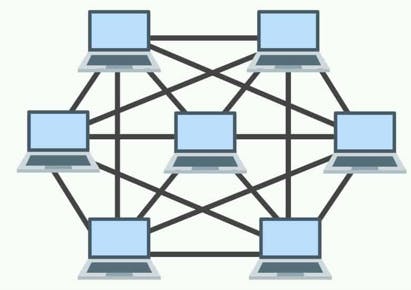
Mesh Topology
Here every device is directly connected to every other device in the network.
Pros and Cons of These Topologies
| Topology | Pros | Cons |
| Bus | Easy to manage, low cost | Data can travel only in one direction at any point in time |
| Ring | Low cost, simple to design | One fault can lead to the failure of the entire system. More devices reduce the performance of the system |
| Star | Scalable and Durable, devices can work independently | If the Central Hub fails the entire system fails to operate |
| Tree | Easy to manage, Scalable and Centralized Management | Expensive and if the higher-level systems fail, lower-level systems connected to them stop working |
| Mesh | High-Speed data transfer, Communication of devices with each other is easy | The high cost of cable wires makes them expensive, Redundant paths increase fault tolerance |
These devices are connected through components called Network Devices.
Network Devices
Network devices are hardware or software components used to help communication, data transfer, and network management within a computer network.
There are different types of network devices. They are used based on the requirement and purpose. Some of the generally used network devices are shown:

Geography of Network
There are three main Area Networks that define the geographical scope and connectivity across devices:
LAN (Local Area Network): It is a network that spans a small geographical area, such as an office building, school, or home. LANs are used to connect devices nearby, typically within a single location. It may use cables, ethernets, or WiFi.

MAN (Metropolitan Area Network): A network that covers a larger geographic area, such as a city or a metropolitan area. MANs connect multiple LANs using high-speed connections, often fibre optics. MANs are commonly used by organizations or Internet service providers to interconnect their local networks across a city.
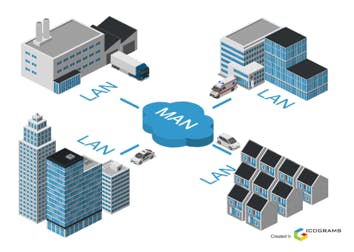
WAN (Wide Area Network): This network covers a larger area, such as a country. It connects multiple LANs or MANs using long-distance communication links.

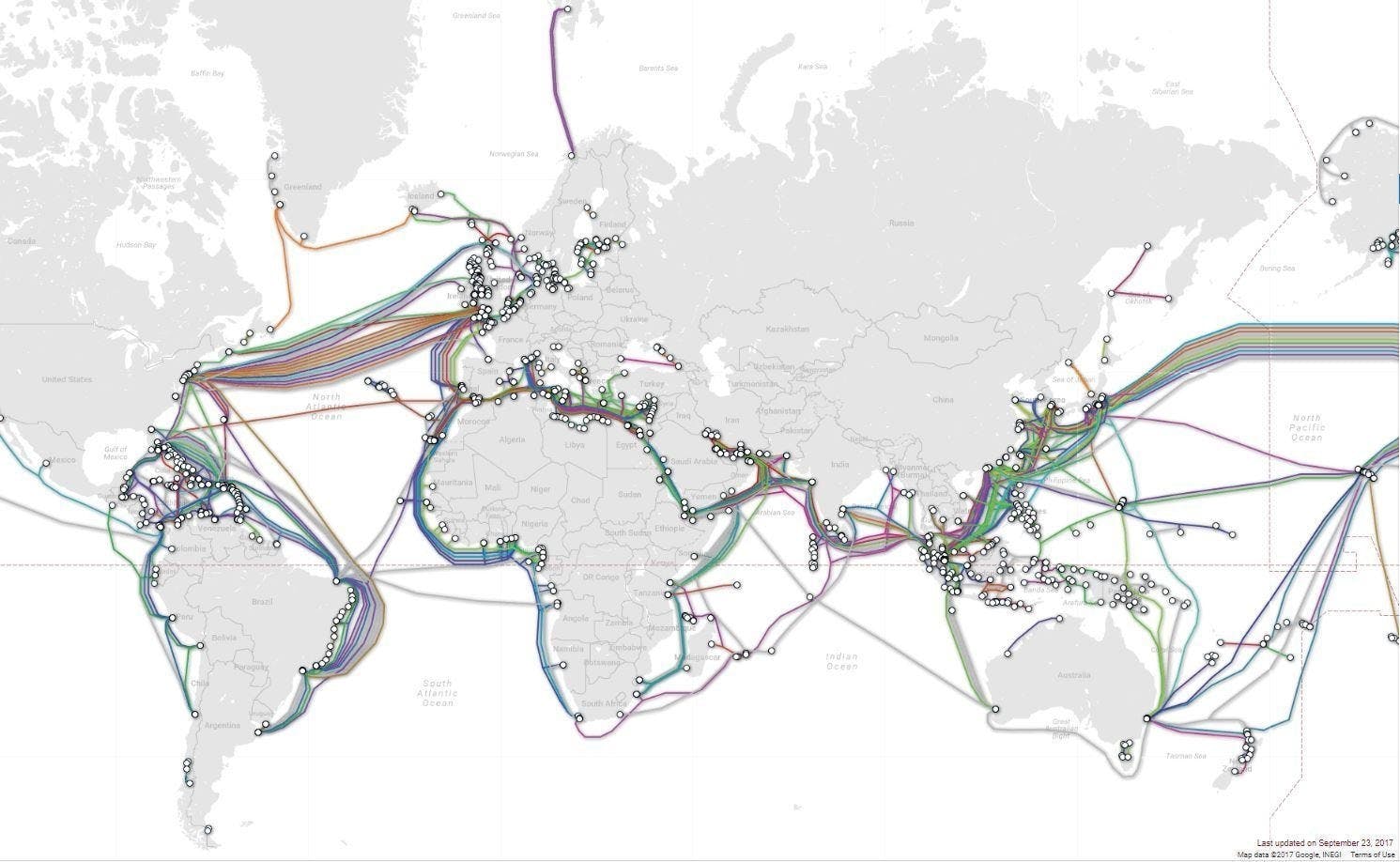
Where does the Internet reside, in Clouds or somewhere else? 🤔
‘People think that data is in the
cloud, but it’s not. It’s in the ocean.’
Communication over large geographical locations and the transfer of data occur at the seabed.

This occurs through very large and thick optic fibre cables connecting various continents and countries around the globe. You can see the image below which shows how these wires are laid across the oceans.
How does the Internet work?
The internet operates on a certain set of protocols and standards that govern how data is transmitted and exchanged between devices. The key protocols used on the Internet include the Transmission Control Protocol/Internet Protocol (TCP/IP).
What are Protocols?
A protocol is a set of rules that governs how computers communicate with each other on the Internet. These protocols define the format, sequence, and meaning of data exchanged between devices, ensuring compatibility and efficient communication.

There are many different types of Internet protocols, each with its own specific purpose like HTTP used in web browsing, FTP for file transfer and much more.
But you might be wondering how the data gets transferred, who transmits and who receives the data. This brings us to a very basic and important concept of Client-Server Architecture.
Client-Server Architecture
This is the simplest way of data transfer between devices.
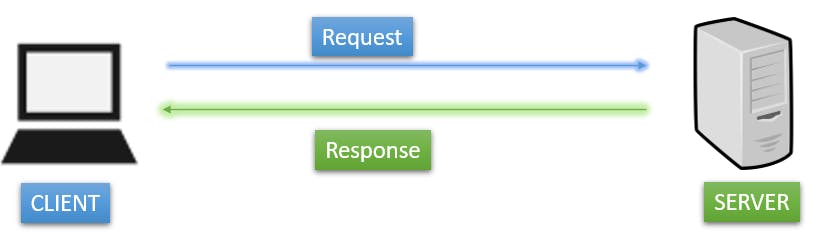
The client, typically a user's device, requests services or resources from a server, which can be a dedicated computer or system that provides those services.
For example, if you want to connect to google.com, you as a user send a request to the Google servers and they respond with the webpage and the other necessary data.
While covering HTTP requests we will see the above process in detail.
Now, we have been talking about data transfer through devices. How are these devices identified over this large network of millions of devices, making sure that the data reaches its correct location? They are identified by IP Addresses and Port Numbers.
IP Addresses and Port Numbers
What are IP Addresses?
IP addresses (Internet Protocol addresses) are unique numerical identifiers assigned to devices connected to a network. It is used to route data to the correct destination.
Your ISP (Internet Service Provider) assigns the IP to your device. In India, there are companies like TATA, Airtel, and Reliance Jio, that act as ISPs for consumers.
curl ifconfig.me -s #command to see IP address assigned to your device
There are two primary versions of IP Addresses, IPV4 and IPV6.
IPV4 and IPV6
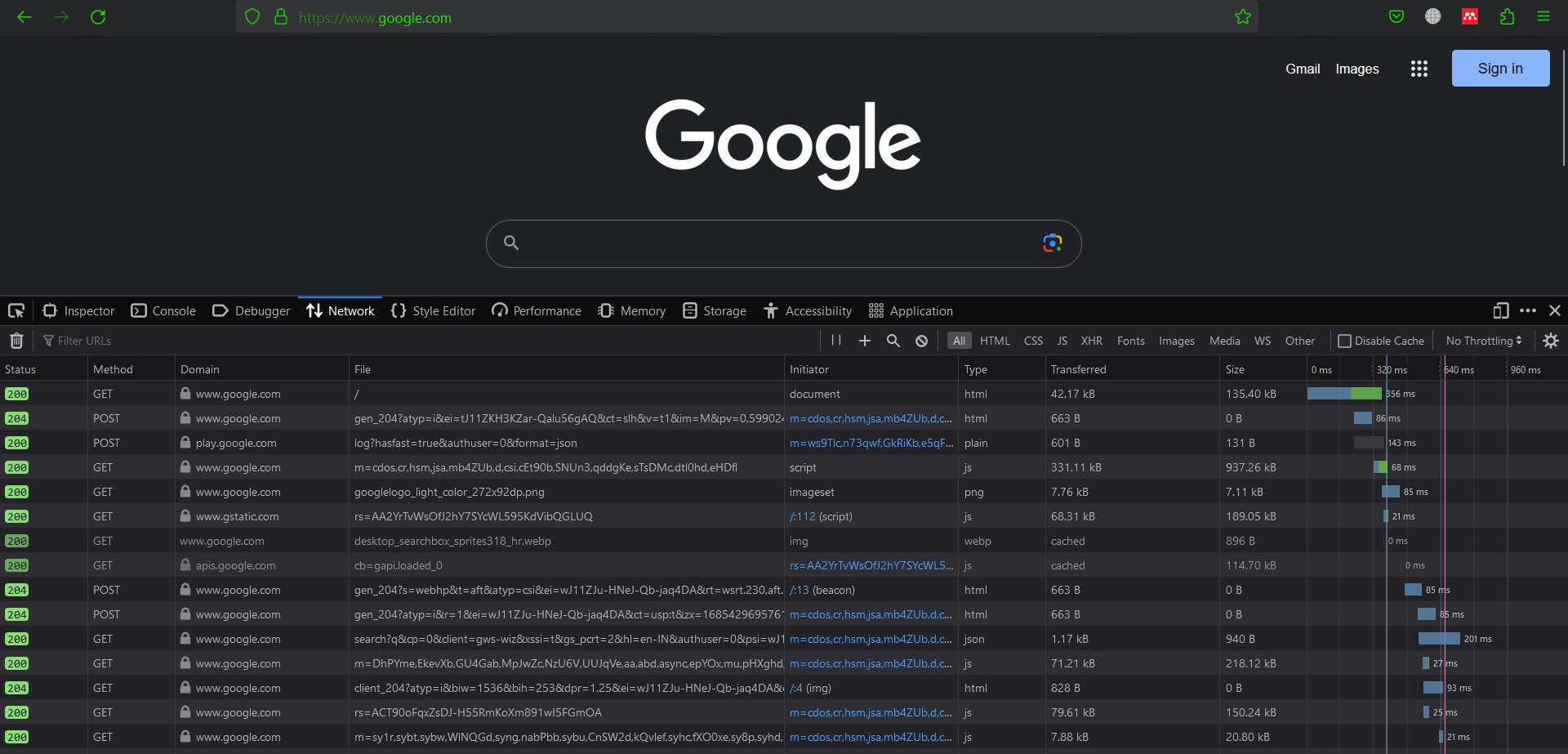
IPV4 is a 32-bit number with 4 fields, each field represents a 8-bit binary number.
Network ID represents to which network our device belongs, it is also known as subnet ID. And the device ID is used to identify the device among the same networks.
IPV6 is a 128-bit number with 8 fields, each field is a alphanumeric value (hexadecimal value) that represents a 16-bit binary number.
eg:- 3002:0bd6:0000:0000:0000:ee00:0033:6778
IPV4 is still widely used, but IPV6 was made seeing the rapid increase of devices, seeing that IPV4 addresses might face shortage someday.
What is the process of assigning the IP address?
There are two ways of assigning IP Addresses:
- Static IP: IP addresses are manually configured by network administrators on devices like servers, routers, or printers which requires consistent and predictable network access.

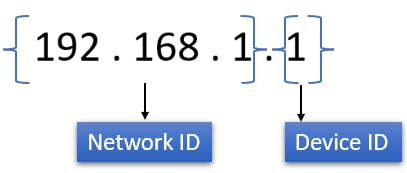
Dynamic IP: IP Addresses are assigned to the devices using the DHCP (Dynamic Host Contol Protocol) which is a network management protocol. DHCP automatically assigns IP addresses to devices.
DHCP servers manage a pool of available addresses and lease them to connecting devices. Upon client connection, client devices request an IP address and receive one from the server, along with other network settings. Leased addresses are returned to the pool after a specific period for reuse.
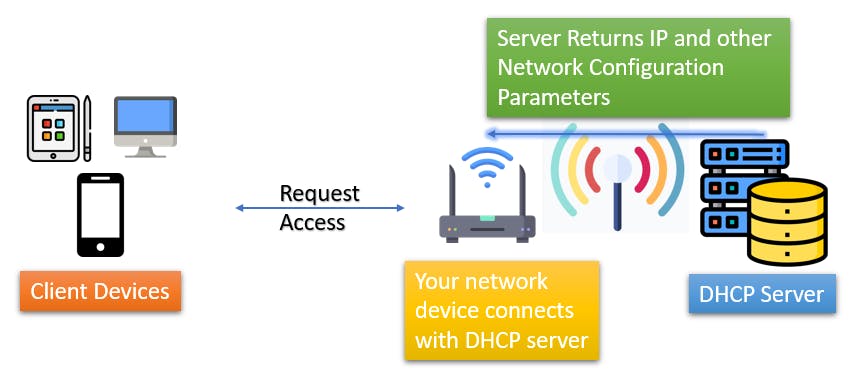
There is a difference between the IP Addresses which are assigned to the devices and what the routers or the network device use. Let's understand using a diagram:
The External IP Address is assigned to our router to identify over the Internet by the ISP, which is also called the Global IP Address. The devices connected to the side of the router in our local network are assigned Internal IP Addresses, which are the local IP Addresses for our devices.
These Local IP Addresses are either assigned statically or dynamically.
What are Port Numbers?
A port number is a 16-bit unsigned integer that identifies a specific application or process on a computer. Each application or process is assigned a unique port number, which allows multiple applications to run simultaneously on the same device.
Each communication endpoint (i.e., a combination of IP address and port number) represents a distinct service or application. They range from 0 to 65535 (216 ).
Reserved ports: 0 to 1023.
Eg:- 80 is reserved for HTTP, 25 is for SMTP.
Registered Ports: Port numbers from 1024 to 49151 are known as registered ports. These ports are assigned by the Internet Assigned Numbers Authority (IANA) upon request from organizations or developers for specific applications or services.
Dynamic or Private Ports: Port numbers from 49152 to 65535 are dynamic or private ports. They are available for temporary or ephemeral use means used by client applications when establishing connections with servers.
We will go into the details of IP and Port numbers and their combination for communication when learning about TCP/IP Protocol in detail.
Data Transfer Through The Internet
In networking, data is digital information that is transmitted, processed, and stored. It can include text, images, videos, audio, files, and more.
The data travels through a process called data transmission. Data transmission is the transfer of digital information from one device or location to another over a network or channel. It moves data in the form of bits or bytes from a source to a destination.
Let's take a look at how it travels:
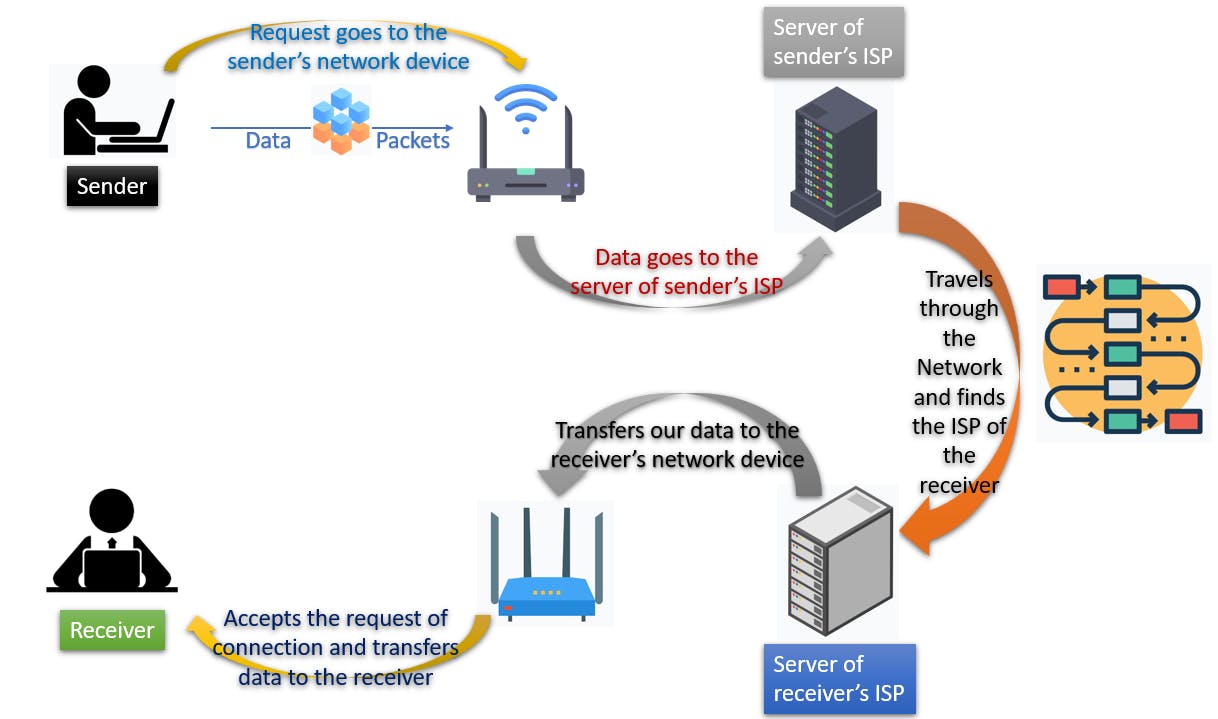
Data travels in the form of chunks called data packets. The above process is a general scenario of how the data gets transferred over the internet.
Some Crucial Terminologies for Computer Networking
Sockets: They are endpoints for communication between two processes. They enable applications to send and receive data through network connections. It is a combination of IP Address and port numbers.
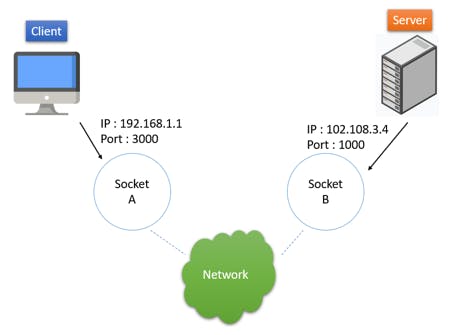
DNS: (Domain Name System) It is a system that translates human-readable domain names into machine-readable IP addresses. These servers store and manage the mapping between domain names and IP addresses, facilitating the routing of network traffic.
Cookies: Cookies are small data pieces stored on a user's computer by websites. They track preferences, store login details, and personalize browsing.
Checksum: It is a value that is calculated from a piece of data and used to verify the integrity of the data. If the checksum does not match, then the data has been corrupted.
3-way handshake: It is a method used to establish a reliable connection between two devices over a network, particularly in TCP/IP-based communication.
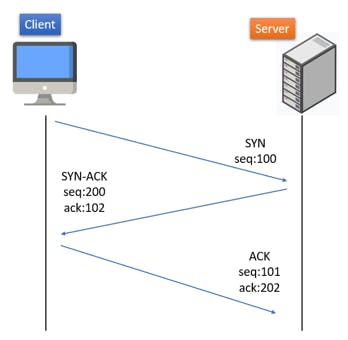
The client sends a SYN packet to the server.
The server responds with an SYN/ACK packet.
The client responds with an ACK packet.
MiddleBoxes: Devices that sit between two computers and perform some sort of processing on the data that is being transmitted. They are often used to filter or block traffic, or to provide security services.
Control Plane: It is the part of a network that is responsible for managing the network. It includes devices such as routers and switches, and it is responsible for routing traffic and keeping track of the network topology.
Timers: Used to keep track of time in a network. They are used for a variety of purposes, such as to keep track of the time that a connection has been idle or to resend packets that have not been acknowledged.
Congestion Control: It is a technique that is used to prevent a network from becoming overloaded. It works by slowing down the rate at which data is transmitted when the network is congested.
Packets: They are the basic unit of data that is transmitted over a network. They are small chunks of data that are wrapped in a header that contains information about the packet, such as its destination and its length.
Network Models
Computer Network Models include software and hardware components that are used to send and receive data from one device to another.
The hardware is the physical equipment that is required to send and receive data while software defines the set of instructions that uses the hardware equipment for data transmission. So now, let's directly jump into the two very important models in Computer Networking.
Before we move on to the models make sure to cover the above topics that are covered so that it can be very easy to absorb the process and understand these models.
OSI Model
The OSI (Open Systems Interconnection) model is a conceptual framework that defines the functions and interactions of network protocols and services. It consists of seven layers.
Application Layer : This layer provides network services to the user software applications. It is the closest layer to the user. It uses different protocols like HTTP, FTP, SMTP, etc. to enable application-specific functionalities.
Presentation Layer : Data from the application layer is sent to this layer and the conversion of data into Machine Readable Format takes place here. Also processes like Encoding, Encryption, and Compression of data are done before sending further.
Session Layer : This layer helps in setting up and managing the connection. Before setting up the session it authenticates and authorizes to the server. It allows applications on different devices to maintain communication sessions. Enables sending and receiving of data, followed by termination of sessions.
Transport Layer : Transports the data to the receiver using protocols like TCP and UDP. Here the data is divided into small data units called segments. And every segment contains the source and destination port number and sequence number.
It also controls the flow of data. And perform error control procedures so that the data does not get lost. It adds checksums to every data segment.
Network Layer : This layer works for the transmission of data received from one network to another. The routers reside in this layer.
The segments of data that it receives are then assigned the IP address of the sender and receiver and form an IP Packet. This is done so that the data reaches its correct destination. Routing is performed here, moving one data packet from source to destination by selecting the best possible path available.
Data Link Layer : In this layer physical addressing of data happens which means to decide which device to send the data to. These physical addresses are what we call MAC Addresses of devices.
These MAC Addresses of the sender & receiver are assigned to the data packet to form a frame.
Physical Layer : This is where the hardware section resides. It may be wires, cables, or any mechanical medium to transport the data.
The frame which it received gets converted into electrical signals in the form of bits and these bits of data are then transferred to the required local device.
This same process happens for sending the data from the sender's application and when the receivers receive the data it is followed again.
The OSI model is a significant reference for network design and implementation. While not directly implemented in the Internet's architecture, it has influenced the development of network protocols, including the widely used TCP/IP model.
TCP/IP Model
TCP/IP (Transmission Control Protocol/Internet Protocol) model is a widely used networking model that provides the foundation for communication on the Internet. It consists of five layers.
Application Layer : This is the layer where the user interacts with the application. Consists of the application on the user's device. Here is where our Client-Server Architecture is implemented. It also uses various protocols for transfer to enable application-specific functionalities.
Transport Layer : It is located on the user's device. This layer is responsible for taking the information (data) from the application to the network using multiplexing and network to an application using demultiplexing.
This layer also takes care of the multiple types of data you send over the internet. It provides abstraction and congestion control.
It uses the method of checksum and timers to send the data packets without any loss.
Connections with networks are established through a 3-way handshake.
Network Layer : It is responsible for the transfer of data from one network to another. This is where our routers reside. Routers in the network have their network addresses (network IDs).
These routers check their routing tables which contain the destination network address to send the data packets further using the best available path to network devices. This transfer is done by hop-by-hop forwarding.
These data packets also interact with Middle Boxes which provide an extra layer of security for transfer.
Data Link Layer : In this layer the data packets that come with the information of source and destination IP addresses get exchanged with the devices.
Physical Layer : Here the hardware part of the devices converts the data received from the Data Link Layer into binary format and provides it to the required application.
Conclusion
I have tried to make this article in the most beginner-friendly way and simple as possible and break it down with relevant examples. Any suggestions for improvement are always appreciated.
Hope you found this article helpful! 😄